Password cracking and how it can help your organisation
Password cracking can be an invaluable tool when it comes to checking your organisation's password hygiene.
It's been said a few times that "passwords are dead", but no-one has come up with a successful replacement yet. Sure, we've got biometrics in the form of fingerprint and face unlock but these still have a PIN or password as a fallback. Given passwords are secret you have no easy way to know the quality of passwords in use by your employees - that's where password cracking comes in. We can use password cracking to audit our organisation's password health.
How are passwords stored?
Password storage varies from system to system. Some systems, particularly older ones, store passwords in plain text alongside the username:
username | password
------------------|-------------
jonathan | fountainpen
hermione | ronald
albus | phoenixThe problem with this approach is that anyone with the ability to view the password database could take someone else's credentials and pretend to be them. To help combat this, passwords started to be "hashed", a mathematical process where a string of text is taken, an algorithm run, and a new text string outputted. The hash is "one way", meaning you can't take the hash and undo it:
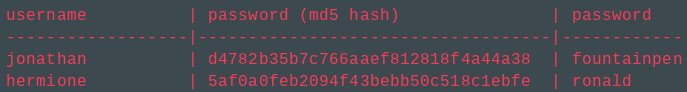
username | password (MD5 hash)
------------------|---------------------------------
jonathan | d4782b35b7c766aaef812818f4a44a38
hermione | 5af0a0feb2094f43bebb50c518c1ebfe
albus | b3d97746dbb45e92dc083db205e1fd14Hashes can be cracked (see below) so the process changed again to include a "password salt", an additional piece of information known to the system. The salt would be added to the password, much like salt is added during cooking, to try and make password cracking more difficult.
These are just a few examples, there are many more password storage techniques.
What is "password cracking"?
Password cracking is the process of obtaining a password that's been stored by a computer system. For passwords stored in plain text this is a simple case of copying the data (so I wouldn't call it cracking) whereas the real cracking comes when working with hashed passwords.
As a hash is cryptographically one way, it's not possible to just run an algorithm over the hash to get the original input value. Instead it's necessary to take a list of words, phrases or text strings and hash them, seeing if the hash matches.
For example, consider the password hash 1660fe5c81c4ce64a2611494c439e1ba. This is an MD5 [1] hash, so we take a word list (e.g. "password", "hell", "hello", "apple" and "jennfier") and hash each word in turn, comparing the result with the target hash:
password
5f4dcc3b5aa765d61d8327deb882cf99
hell
4229d691b07b13341da53f17ab9f2416
hello
5d41402abc4b2a76b9719d911017c592
apple
1f3870be274f6c49b3e31a0c6728957f
jennifer
1660fe5c81c4ce64a2611494c439e1baFrom this exercise we can see the password was "jennifer". Password cracking tools like John the Ripper perform these calculations and comparisons at over hundreds of passwords a second (the actual speed depends on the hardware being used). Note that "hell" and "hello" had completely different hashes, despite almost being the same word.
You can read more about password cracking on Wikipedia.
Is it legal and ethical?
Legality depends on where you got the password hashes from. By law (in England at least) it's permitted to hack or test the security of a system that you own, or have the system owner's permission to target. By extension it would be legal for me to audit the passwords on a system I owned (for example my company's Active Directory).
If I hacked into another system and downloaded the password hashes, perhaps by SQL injection I'd be guilty of illegally accessing a computer system. Similarly I could't then crack those hashes.
Ethics can get a bit sticky here. You're going to see passwords that are used by people you know, that they may use elsewhere. Some passwords may be harmless, but others may give away more than you wanted to know. Treat everything you see sensitively.
What about lockouts?
Many systems now lock an account in the event of a brute force attack, where multiple passwords are attempted for an account in a short space of time. Some environments I've worked in will temporarily lock out an account after three failed attempts. Clearly we don't want to lock out our users while running the audit.
Fortunately we're not running our audit against the live system, we're performing our cracking process against the hashes we've obtained. Our cracking is being done offline so there's no concern over downtime caused by a brute force attack.
Are there risks?
Short answer: yes.
Consider the scenario, I take a list of password hashes and begin to crack them. Some will be cracked fairly quickly, others will take time, but ultimately I'm going to end up with a list of usernames and passwords:
username | password (MD5 hash) | password
------------------|-----------------------------------|------------
jonathan | d4782b35b7c766aaef812818f4a44a38 | fountainpen
hermione | 5af0a0feb2094f43bebb50c518c1ebfe | ronaldThat list must be protected, otherwise your organisation is at extreme risk - if someone finds the list they have the keys to your kingdom. Given the high prevalence of password re-use it's possible you've now also got someone's Facebook password too (don't try it).
What next?
Once we've got our cracked passwords we can analyse them to look for patterns and then educate colleagues in good password practice. Looking at the examples above, the passwords aren't very long and are dictionary words or common names that are likely to have been on a word list. Guidance is currently to use an easy to remember, longer, password that's hard to guess, perhaps made from three random words. An example might be 2 Laptop Tree Roadworks. It's not a horrible jumble of letters and numbers (wde5gyma!s) and is quite long . As a result of the words being random, and not related (don't pick Cadbury Chocolate Bars 5), we've got a good password that's unlikely to be on a word list. A completely random stream of characters is also good, but quite a pain if you have to type it in!
The audit is most likely to find some skeletons in the closet - problems we didn't know about (or had chosen to forget). Use the audit as a good moment to clear out the skeletons and educate people. It's worth remembering that poor passwords still pass technical controls for passwords too. Passw0rd is a really bad password but if your technical control (password policy) says a password must have a minimum of 8 characters, capital letter and a number it'll still pass.
Most importantly, every account whose password was cracked needs to be reset - don't leave the password unchanged!
Have you ever performed password cracking?
Yes. A few years ago I performed a password audit of a client's Active Directory environment. Active Directory doesn't use MD5 hashes for passwords, unlike my examples here, but it's still possible. Within thirteen (13) seconds I had passwords for 169 accounts, largely due to password re-use across the organisation. This is common when a team is responsible for creating accounts or resetting passwords, and users don't then change them. Speaking to other penetration testers it's not uncommon to find the month and year (January2018) or season and year Winter2017) or the company name.
We immediately ran a programme to educate users which massively helped with the problem. Another audit is needed to see if the education worked though.
Password managers
The best password is one that you don't know, and can't remember, and a good password manager will help with that. Keepass or LastPass are two examples that I've used and both can create strong, long, passwords. If you're using the same password in multiple places, or are concerned about your own password practices, I'd recommend you give a password manager a go.
The bad guys do it too
It's worth remembering that all cyber security tools are dual purpose - they can be used for good or evil. The bad guys are performing password cracking too so it's in your best interests to protect your systems from exploits that would allow an attacker to get a list of your password hashes. If all your users (or all your) passwords are good quality passwords it'll take an attacker a very long time to break the hash.
[1] MD5 is a hash algorithm that's considered broken now, as it's possible to get the same hash from two different inputs. More on Wikipedia.

